nfrastructure as Code (IaC) has rapidly become a cornerstone of modern IT management and cloud adoption strategies. It’s a trend that has gained significant traction among CIOs (Chief Information Officers) and other enterprise leaders due to the powerful benefits it offers for managing infrastructure in a scalable, consistent, and automated way. Here’s why it’s important and why it’s trending for enterprise IT journeys:
1. Automation and Efficiency
— Manual Processes Are Error-Prone: Traditionally, infrastructure was manually provisioned and configured, which led to human errors, inconsistencies, and misconfigurations. With IaC, infrastructure provisioning becomes automated, reducing the risk of errors and inconsistencies.
— Faster Deployments: IaC enables automated, repeatable processes, so infrastructure can be provisioned in minutes rather than days or weeks. This increases the speed at which companies can develop and deploy new applications and services.
— Consistency: With IaC, infrastructure is defined in code, meaning it’s defined and managed the same way every time. This reduces the “it works on my machine” issue and ensures consistency between development, testing, staging, and production environments.
2. Scalability
— Dynamic Infrastructure Scaling: Enterprises need infrastructure that can scale quickly with changes in demand. IaC allows for the definition of scalable infrastructure configurations that can automatically adjust based on load (e.g., automatically scaling resources based on demand).
— Handling Complex Environments: As businesses grow, so do their infrastructure needs. IaC enables the management of complex environments, with multiple interdependencies, in a controlled and scalable manner, without relying on human intervention to maintain the scale.
3. Cost Efficiency
— Resource Optimization: By automating infrastructure management, businesses can reduce the over-provisioning of resources. IaC allows teams to define the minimum infrastructure needed and scale it as required, preventing wasteful spending.
— Self-Healing Infrastructure: With IaC, infrastructure can be automatically repaired when something goes wrong, reducing downtime and the need for costly interventions from support teams. For example, if a service fails, IaC can automatically replace it based on the predefined configuration.
— Infrastructure in the Cloud: Cloud providers often charge based on resource usage. IaC allows businesses to provision resources dynamically, avoiding unnecessary costs while ensuring resources are only allocated when needed.
4. Speed and Agility in Development
— Faster Time to Market: IaC enables rapid provisioning and reconfiguration of infrastructure, reducing the time it takes to deploy applications or services. With faster deployment pipelines, development teams can test and release new features quicker, leading to faster innovation and time to market.
—Self-Service Infrastructure: Developers and teams can request the infrastructure they need through predefined templates (IaC code), making the process more agile. Teams can provision and modify infrastructure without relying on the operations team, increasing self-sufficiency.
5. Version Control and Traceability
— Infrastructure as Code is a Version-Controlled Artifact: IaC allows infrastructure definitions to be stored in version control systems like Git. This enables teams to track changes over time, collaborate on infrastructure code, and audit who made changes and why. This level of traceability and version control ensures accountability.
— Rollback and History: Since infrastructure configurations are treated like code, you can track every change made to the infrastructure. If something goes wrong, you can easily roll back to a previous stable version, reducing risk during infrastructure changes or failures.
— Configuration Management: IaC tools integrate well with configuration management systems, ensuring that all services are configured according to the latest code, reducing drift and keeping everything in sync across environments.
6. Security and Compliance
— Enforced Best Practices: By treating infrastructure as code, security best practices can be incorporated directly into the infrastructure definitions. For example, network security groups, access control policies, and firewalls can be specified in code, reducing the risk of manual security misconfigurations.
— Automated Audits and Compliance: As infrastructure code is stored in version control, it can be reviewed, and automated checks can be run to ensure compliance with industry standards and internal policies. Additionally, tools like Terraform or Ansible allow for security audits as part of the deployment process, ensuring that only compliant and secure configurations are applied.
— No Drift: IaC helps prevent “configuration drift,” which occurs when changes are made outside the controlled codebase, often bypassing security checks. With IaC, every change is recorded and can be verified, improving security posture.
7. Disaster Recovery and High Availability
— Automated Disaster Recovery: In the event of an outage or disaster, IaC can be used to quickly recreate the infrastructure in a new region or cloud provider. By having infrastructure defined as code, businesses can easily recover from disasters with minimal downtime.
— Consistency Across Regions and Environments: Using IaC ensures that infrastructure across different environments (dev, staging, production) is consistently configured. This consistency allows for better disaster recovery strategies, as the exact same infrastructure can be redeployed to restore service.
8. Improved Collaboration Between Development and Operations (DevOps)
— Bridging DevOps Teams: With IaC, development and operations teams can collaborate more easily, as infrastructure and application code are now managed together. IaC provides a common language and understanding between developers and operations engineers, reducing friction and improving collaboration.
— Faster Feedback Loops: By having automated infrastructure provisioning, development teams can quickly get feedback on how their applications behave in the real-world environment. Operations teams also get faster feedback when issues are detected with infrastructure, improving overall efficiency and responsiveness.
9. Cloud-Native and Multi-Cloud Flexibility
— Cloud-Native Operations: As more enterprises adopt cloud environments, IaC becomes essential for managing cloud-native infrastructure. IaC tools like Terraform, AWS CloudFormation, and Azure ARM templates make it easier to manage complex cloud infrastructures.
— Multi-Cloud Flexibility: Many enterprises are now adopting multi-cloud strategies to avoid vendor lock-in and improve redundancy. IaC allows for the seamless management of infrastructure across different cloud providers (e.g., AWS, Azure, Google Cloud), enabling businesses to have flexible and resilient cloud architectures.
Today it is quintessential for every enterprise to now adopt IaC as part of their infrastructure automation journey. Most of them have already onboarded and the next few are inline primarily for the following reasons.
- Digital Transformation: As enterprises embrace digital transformation, IaC becomes an essential part of enabling modern IT infrastructure. It aligns well with the adoption of cloud technologies, automation, and agile methodologies.
- Cost Control and Agility: CIOs are constantly looking for ways to reduce costs and increase agility. IaC allows enterprises to do more with less — automating manual processes, enabling rapid provisioning, and ensuring efficient resource use.
- Business Continuity: In a world where downtime can be costly, IaC ensures that the infrastructure is more resilient and recoverable. By having infrastructure as code, CIOs can ensure that their teams can quickly respond to changes or failures, minimizing disruptions to business operations.
- Security and Governance: With an increasing focus on security and regulatory compliance, IaC allows enterprises to embed security policies directly into infrastructure. This reduces the likelihood of errors and ensures that infrastructure remains compliant with industry standards and policies.
- Competitive Advantage: Finally, the ability to scale quickly, innovate faster, and respond to customer needs more effectively provides a competitive advantage. This is why CIOs see IaC as a key component of their strategic IT goals.
Here is a crucial comparison of the various Infrastructure as Code (IaC) tools that are widely used.

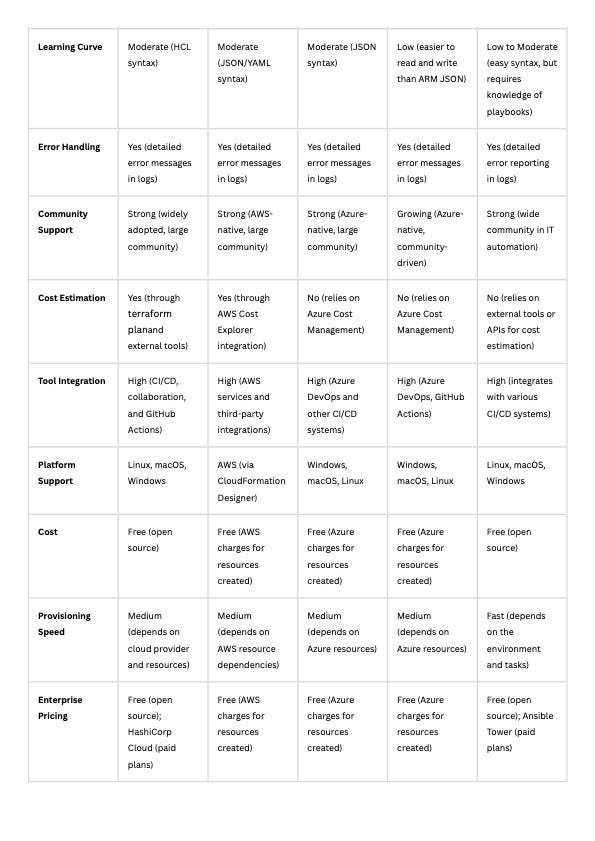
Terraform gives you a clear advantage by…
State management is a **critical** feature in Terraform because it allows Terraform to **track and manage the infrastructure** it creates and updates. Here’s a detailed breakdown of why state management is so important when using Terraform:
- Tracking Infrastructure Changes
— State File: Terraform maintains a state file that holds the current state of the infrastructure (what resources exist, their properties, etc.). This is necessary because Terraform operates on a declarative model, where you define the “desired state” of your infrastructure, and Terraform uses the state file to compare the actual infrastructure to the desired state.
— Terraform Plan: The state allows Terraform to know the current setup and make decisions about what needs to be created, modified, or destroyed when you apply new configurations. Without this information, Terraform wouldn’t be able to figure out what has changed since the last execution. - Preventing Drift and Ensuring Consistency
— Drift Detection: Over time, infrastructure resources might change outside of Terraform (e.g., manual updates or changes made through the cloud provider’s console). The state file helps Terraform detect these changes, also known as “drift”, so that it can bring the infrastructure back into sync with the defined configurations.
— Consistency: With the state file, Terraform ensures that the infrastructure remains consistent with the desired configuration. Without this state management, Terraform wouldn’t be able to track whether resources are correctly aligned with the configurations or if they need to be reconciled. - Incremental and Efficient Infrastructure Changes
— Efficient Resource Management: When you apply changes using Terraform, it uses the state file to only modify the resources that actually need changing, rather than recreating or modifying everything from scratch. This efficiency reduces the risk of downtime or unintended consequences during infrastructure updates.
— Execution Plans: By knowing what has been provisioned, Terraform can create an execution plan (`terraform plan`) that shows exactly what changes it intends to make before applying them. This allows for controlled and informed updates. - Collaborative Workflow
— Remote State: When working in a team, it’s crucial to have a shared, consistent state that everyone can access and update. Remote state backends (like AWS S3, Azure Storage, etc.) are commonly used for this purpose. They allow multiple team members to work on the same infrastructure without conflicts, as everyone will have access to the latest state.
— Locking State: Terraform can lock the state file when changes are being applied, preventing others from making conflicting changes at the same time. This is especially important in large teams working on complex infrastructures. - Resource Dependencies and Graph Construction
— Dependency Management: Terraform automatically generates a resource dependency graph based on the configuration and state file. This ensures that resources are created in the correct order and that Terraform can track dependencies between resources (e.g., ensuring a database is created before a web server that relies on it).
— Resource ID Tracking: The state file stores important metadata about the resources, such as their unique identifiers (e.g., an AWS EC2 instance ID). Without this information, Terraform wouldn’t know how to manage the resources properly (e.g., to update an existing resource instead of creating a new one). - 6. Infrastructure Scaling and Changes Over Time
— Resource Updates: As your infrastructure evolves (for example, you add new instances, change settings, etc.), Terraform relies on the state to keep track of these changes and ensure that subsequent updates are applied correctly.
— Scaling Infrastructure: Terraform can scale infrastructure up or down based on the changes made to your configuration. By maintaining state, Terraform knows how many instances or resources exist and ensures that any scaling operation is accurately reflected in the cloud provider. - Backup and Recovery
— State File Backup: Having a proper backup of the state file ensures that you can recover and restore your infrastructure in case something goes wrong. Without the state, you would lose all the information about your deployed infrastructure, and managing or updating it could become challenging.
— Disaster Recovery: If infrastructure gets deleted or corrupted, the state file can be used to reapply the existing infrastructure and prevent manual reconfiguration.
8. Cross-Environment Management
— Managing Multiple Environments: Terraform state files can be managed separately for each environment (e.g., dev, staging, production) to avoid conflicts. This allows teams to deploy, update, and manage multiple environments independently, all while keeping them in sync with their respective configurations.
— Workspaces: Terraform supports the use of workspaces, which are like isolated environments that allow you to have separate state files for different configurations or stages of the infrastructure (dev, prod, etc.). This further ensures that your changes don’t overlap between environments.
In summary, state management in Terraform is essential because it enables Terraform to:
– Understand the current infrastructure configuration.
– Efficiently manage and apply incremental changes.
– Prevent drift and ensure the desired state is maintained.
– Provide a collaborative, safe, and consistent way of managing infrastructure across teams.
– Enable backup, recovery, and scaling of infrastructure over time.
Without state management, Terraform would have no context about the current infrastructure, and it would be nearly impossible to reliably manage and automate changes in a dynamic, complex environment. But it is also important to understand Terraform automates the provisioning and does not automates the management, the accountability of managing the infrastructure still lies with the infrastructure architects and the infrastructure management personnels.
However, I will further explore the common challenges encountered during IaC implementation and highlight how IaC extends beyond just provisioning tools. It encompasses a combination of people, processes, and tools — forming a comprehensive engineering framework. This will be delved into in the upcoming articles. If you find the content valuable or would like to see more articles like this, don’t forget to follow and share!



